
Network-connected technology has become essential to daily healthcare operations, and medical devices are a major aspect of this advancing technology. These devices are integral to improving patient outcomes and the efficiency of care delivery. However, their unique technological features and clinical functions also introduce risk factors. Despite the numerous standards and robust regulatory frameworks throughout the healthcare industry, existing legislation does not address these considerations comprehensively.
Regulatory compliance is an intuitive standard for evaluating a health system's cybersecurity preparedness. While following laws and regulations is crucial, it is not enough to drive a robust medical device cybersecurity program. Managing the unique technological features, clinical functions and capabilities, and risk factors inherent in medical devices helps identify gaps between the regulatory landscape, standards, and the realities that healthcare organizations face in the industry.
The Growth of Network Connectivity
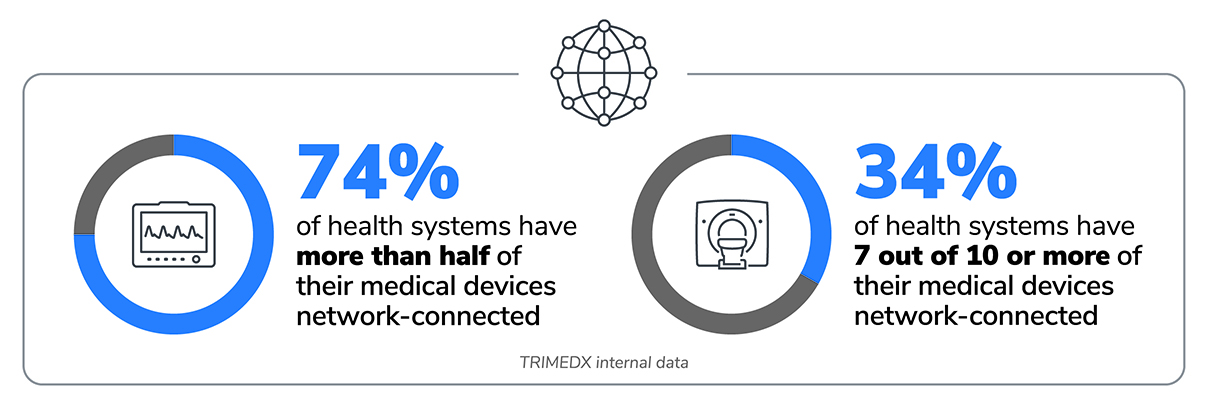
A significant shift is taking place in how health systems utilize their medical devices: 74% of healthcare organizations now have more than half of their medical device inventory connected to networks.1 This trend toward network-connected medical devices is expected to continue and represents remarkable progress in advancing the standard of care. At the same time, it also poses substantial risks if health systems do not implement robust, consistent processes to manage networks and cybersecurity risk. As the number of network-connected devices grows within a hospital, health systems must understand the important role that medical device cybersecurity plays and be prepared to move beyond simple compliance as they embrace new legislation, regulations, and guidelines to develop and implement a robust and effective cybersecurity program.
The Evolving Regulatory Landscape of Medical Device Cybersecurity
The goal of protecting healthcare data predates the proliferation of network-connected medical devices by decades. However, the growth of these technologies has begun to heavily influence the direction of recent legislative action. In many ways, the rapidly evolving challenges of cybersecurity continue to outpace the government’s ability to codify new rules and regulations.
Health Insurance Portability and Accountability Act (HIPAA) - 1996
HIPAA has been a cornerstone of data protection in health care since it was first signed into law in 1996. HIPAA's significance lies in its role as a guardian of patient information. Over time, the government has updated the law in response to evolving technologies and healthcare data management needs. The HIPAA Security Rule requires that covered entities protect patients' electronic protected health information (ePHI), in addition to physical records. The Security Rule demonstrates the ever-increasing focus on cybersecurity, requiring organizations to implement measures to ensure the confidentiality, integrity, and availability of ePHI, including firewalls, encryption, and data backup.
While HIPAA mandates stringent security measures to ensure the confidentiality, integrity, and availability of electronic protected health information (ePHI), it primarily focuses on data protection, not device security. This gap becomes evident when considering that many medical devices serve as data collection and transmission points for ePHI. Devices often store and transmit this data as they play a crucial role in diagnosing, monitoring, and treating patients. Consequently, each network-connected medical device capable of retaining ePHI represents a potential risk for a HIPAA violation. The intricacies of medical device security go beyond HIPAA's purview, emphasizing the need for a more comprehensive approach.
Health Information Technology for Economic and Clinical Health (HITECH) Act - 2009
The Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009 was signed into law as part of the American Recovery and Reinvestment Act of 2009. The HITECH Act encourages healthcare providers to adopt electronic health records, improves privacy and security protections for healthcare data, and increases application and enforcement. HITECH expanded on HIPAA to address the growth of digital technology in healthcare including requirements to report breaches. Like HIPAA, HITECH authorizes the government to impose penalties and fines for certain breaches and, on its own, does not address medical device cybersecurity robustly.
Consolidated Appropriations Act Omnibus Bill, Section 3305: "Ensuring cybersecurity of medical devices" - 2023
In 2022, Congress passed changes to the Federal Food, Drug, and Cosmetic (FD&C) Act to enhance cybersecurity considerations in the FDA approval process for medical devices.2 Starting in 2023, manufacturers must submit plans to the FDA to address cybersecurity vulnerabilities in new devices. They must also implement processes to provide ongoing patching support for devices. Cybersecurity safeguards in medical device design are now requirements for FDA to approve new device submissions. However, these requirements do not affect medical devices that received FDA approval prior to the rule's implementation.
HHS 405(d) Program - 2015
The Health and Human Services (HHS) 405(d) Program is a collaborative effort between industry and the federal government to improve cybersecurity within the healthcare and public health sectors. Established as part of the Cybersecurity Act of 2015, this program provides valuable guidance and resources. However, it lacks enforcement mechanisms or penalties, making it insufficient for driving comprehensive cybersecurity practices.

Going Beyond Compliance by Internalizing Robust Security Standards and Practices
 Ransomware attacks cost healthcare organization in the U.S. $7.8 billion in 2021.5
Ransomware attacks cost healthcare organization in the U.S. $7.8 billion in 2021.5
The cybersecurity landscape within health care is continually evolving, posing challenges that extend beyond the capabilities of legislation and regulation. It is essential to recognize that healthcare data breaches are predominantly technology-driven, with hacking and IT incidents accounting for a significant portion of reported incidents. In August 2023, 83.8 percent of incidents reported to the Office of Civil Rights (OCR) were identified as hacking or IT incidents. 3
In particular, ransomware has dealt heavy blows to healthcare organizations in recent years. Ransomware attacks are distinct from other types of data breaches in that they often don't seek to take ePHI or other sensitive information. Instead, attackers will lock individuals or organizations out of vital technology and records. In health care, this could mean not being able to access patient records or medical devices being disabled. Individual ransomware attacks have cost healthcare organization billions in fines and lawsuits and impacted clinical operations for months. 4,5
Gaps in technology support
Most medical devices in use today are not covered by the FDA requirements implemented in 2023, meaning less patching support for vulnerabilities. Data from 2.1 million medical devices actively managed by TRIMEDX reveal that 68% of vulnerabilities in health systems’ inventories lack validated patches from manufacturers.1
Damages outside of regulatory frameworks
Legislation like HIPAA and HITECH focuses primarily on protecting patient data, which is an essential concern for delivering effective care. However, the direct proximity of medical devices to patients in clinical environments can present a unique risk to physical safety in the event of a breach. If devices that monitor health or directly administer therapies are compromised, it can have potentially life-threatening consequences. The exact level of legal liability when poor outcomes or fatalities are allegedly linked to cyberattacks is not entirely defined by current legislation. However, lawsuits like one in Alabama following the death of an infant who was born at a facility hit by ransomware could mean more financial consequences in the future for health systems.6
Cyberattacks also threaten a resource that is challenging for health systems to measure, yet invaluable: their reputations. The memory of a cybersecurity breach can linger for a long time, especially in highly publicized instances. The impact of eroding trust from communities is not something health systems can afford, both for the sake of their business and, more importantly, for their mission of delivering care to patients.
"Suite blames baby's death on cyberattack at Alabama hospital"
-Associated Press
Steps to Building a Stronger System of Governance
While legislation and regulations play a critical role in setting cybersecurity standards, they are often reactive rather than proactive. Relying solely on penalties and fines is not sustainable for healthcare organizations operating on narrow margins. To proactively address cybersecurity challenges, health systems must establish processes that go beyond legal requirements.
 Implement strong frameworks
Implement strong frameworks
One effective approach is adopting rigorous industry standards, such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework. NIST's framework encompasses five pillars:
- Identify: Develop an organizational understanding to manage cybersecurity risk effectively.
- Protect: Implement safeguards to ensure the delivery of critical healthcare services.
- Detect: Establish activities to identify cybersecurity events promptly.
- Respond: Develop procedures to act when a cybersecurity event is detected.
- Recover: Create plans for resilience and restoration of capabilities or services impaired by a cybersecurity event.
As of 2023, NIST has introduced a new pillar, "Govern," which emphasizes internal governance to guide organizations in carrying out the actions specified in the framework effectively.7 At first glance, this might seem redundant with the already established framework. However, governance is a major driver for implementing every step of a cybersecurity process with consistency. Consistent processes and approaches to cybersecurity are the only ways for health systems that are facing immense financial and operational pressures to track the efficacy of their strategy.
The value of a framework like NIST is that it aligns with laws and regulations and also drives best practices focused on organizational needs. Implementing these types of rigorous standards can help health systems build a culture of understanding that medical device cybersecurity is a priority beyond regulatory oversight, critical to the success and safety of all stakeholders.
Accepting cybersecurity risk as a multifaceted metric
To adopt stronger medical device cybersecurity policies, health systems need to gain full visibility of their inventories. Medical devices are complex, and the risks associated with them are equally intricate. Health systems should consider a wide variety of factors when assessing medical device cybersecurity risk:
- Is a device capable of being connected to a network, and is it currently connected?
- Would an unexpected device failure endanger a patient?
- How will a device failure impact the ability to deliver care?
- Is the device displaying any anomalous network behavior?
- Can the device store ePHI?
- Does the device have known software vulnerabilities?
- Is patching support available from the device manufacturer?
Accepting this complexity empowers health systems to take confident action in understanding their unique risk posture. Establishing strong governance for a medical device cybersecurity program does not replace regulatory compliance; rather, it equips health systems, their staff, and leadership with the tools to protect patients and their organization's reputation proactively.
Close the loop on assessment and action
Despite the number of risk factors health systems must consider, repeated, standardized assessment can make overall risk much easier to understand. Establishing firm risk criteria means that health systems can find methods to quantify and prioritize risk among individual devices. Establishing regular evaluation as a standard operating procedure creates the opportunity for closed-loop improvement as remediations are carried out, and devices change over time. This approach can help health systems track their progress, quickly identify major risks as they emerge, and continuously improve their risk posture. Ultimately, a quantitative, closed-loop method can help health systems stay ahead of the regulatory landscape and proactively manage medical device risk.
While regulatory compliance is essential in mitigating cybersecurity risks in health systems, it is not enough by itself. Health systems must take a comprehensive approach to managing medical device cybersecurity risks by implementing strong internal governance. This will enable them to integrate pursuing compliance with their unique risk posture and cybersecurity need. With an internalized commitment and focus on medical device cybersecurity, health systems can better protect their patients, operations, and reputations.

Sources
- TRIMEDX internal data
- U.S. Food and Drug Administration. (2023, October 4) Cybersecurity. https://www.fda.gov/medical-devices/digital-health-center-excellence/cy…;
- Alder, S. (2023, September 20). August 2023 Healthcare Data Breach Report. HIPAA Journal. https://www.hipaajournal.com/august-2023-healthcare-data-breach-report/…;
- IBM Security. (2023, July 24). Cost of a Data Breach Report 2023.
- Bischoff, P. (2022, October 5). Ransomware attacks on US healthcare organizations cost $20.8bn in 2020. Comparitech. https://www.comparitech.com/blog/information-security/ransomware-attack…;
- AP News. (2021, October 1). Suit blames baby’s death on Cyberattack at Alabama Hospital. AP News. https://apnews.com/article/technology-business-health-alabama-lawsuits-…;
- The National Institute of Standards and Technology. (2023, August 23). NIST drafts major update to its widely used cybersecurity framework. NIST. https://www.nist.gov/news-events/news/2023/08/nist-drafts-major-update-…;



